Brief Profile
Alpha1 IT has experienced resources who have more than 25 years of experience in Information Technology, Cyber Security, and Digital Forensics domain. Worked as CIO/CISO level position with Corporate & MNCs, last appointment was with Hitachi Systems, Japan as Vice President – IT, currently engaged with numerous Govt organizations working for Digital India initiative under Ministry of Information Technology, Govt of India and on the management board of corporate & PSU as VCISO/Advisor.
- Consultant – NeGD (National e-Governance Division, Ministry of IT, Govt of India)
- Consultant – NISG (National Institute of Smart Governance, Ministry of IT, Govt of India)
- Member – Cyber Security core Group , CII (Confederation of Indian Industries)
- Member – National Committee of e-Commerce , CII (Confederation of Indian Industries)
- Auditor – CERT-IN Empanelled Auditor
- Member – FICCI / ASSOCHEM / PHD Chambers / DSCI
- Author – Books "Cyber Security Hygiene" | “Essentials of Cyber Security”
Our Offerings
CONSULTING
SOLUTIONS
MANAGED SERIVCES
TRAININGS
CONSULTING
Identifying the client's needs
Ransomware/Malware Solution
VAPT/ISO Audits/Compliances
End User Hygiene
SOLUTIONS
Conducting a risk assessment
Web Security Protection
SOC–Security Operation Centre
Technical Trainings on security solutions
MANAGED SERIVCES
Developing & Implementing a plan
Threat Intelligence & Hunting
VCISO–Virtual Chief Information Security Officer
Certification Trainings for employees
TRAININGS
Ongoing support
Encryption of Data at Rest & in Motion
Security Infra Maintenance
Attack simulation Training for employees
TYPES OF VAPT SERVICES
Application VAPT
Server configuration audit Database review Application architecture review Server hardening Code review
Mobile App VAPT
Server configuration audit Database review Application architecture review Server hardening Code review
Infrastructure VAPT
Network architecture review Cloud architecture review Configuration audit Internal audit monthly Policy review
API Testing
Edge Testing, Sensor / Device Operability Testing Security & Network Testing End user Application Testing
Database Testing
Server configuration audit Database review Application architecture review Server hardening Code review
IoT Cyber Security
Server hardening review Database security testing Server configuration audit API vulnerability assesment
Standards & Methodologies
- NIST 800-115
- OWASP (Mobile) Security Testing Guide
- OWASP Mobile Application Security
- Verification Standard
- PCI DSS
Tools
- Tenable Nessus
- Burp Suite Pro
- Metasploit Framework
- Kali Linux
- Proprietary Tools
Our Audit Methodology
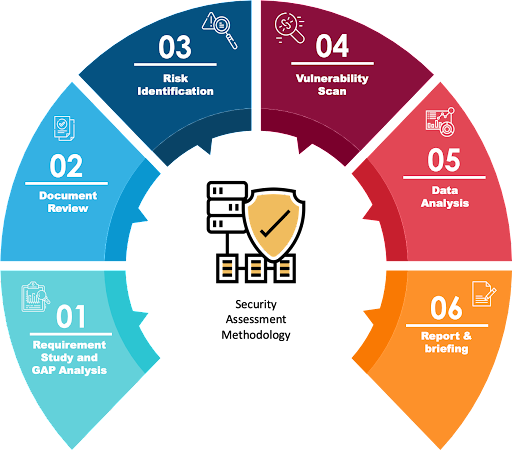
Road Map - Cyber Security Consulting
Identifying the client's needs
- Consultancy begins by working with the client to understand their specific needs and concerns in terms of cyber security.
- This will involve reviewing the client's current security practices and identifying any weaknesses or areas for improvement.
Conducting a risk assessment
- The consultant will then conduct a risk assessment to identify potential vulnerabilities and threats to the client's systems and data.
- This will involve conducting penetration testing, analyzing the client's network and device configurations, and Auditing/ Reviewing their policies and procedures.
Developing a plan
- Based on the findings of the risk assessment, the consultant will work with the client to develop a plan for improving their cyber security posture.
- This will include recommendations for updating policies and procedures, implementing new security technologies, and providing exhaustive counter measures.
Implementing the plan
- The consultant will then help the client implement the recommendations in the security plan,
- Including assisting with the deployment of any new technologies. And providing guidance on how to follow best practices for cyber security.
Ongoing support
- The consultant may also provide ongoing support to the client to ensure that their cyber security posture remains strong over time.
- This may involve conducting regular risk assessments and providing guidance on new threats and vulnerabilities as they arise.
Cyber Security Advisory Activities - Brief
Our Team of veteran CISOs assigned as cyber security consultants are fully dedicated to provide 360⁰ security protection to SMEs and large enterprises, and by leveraging from their industry experience will reduce your specific cyber security risk profile with a strategic approach
1. Take Care About Information security leadership
2. Security Point-Of-Contact for All Issues
3. Building security Strategy & Roadmap
4. High level Cost estimates for budgetary purposes
5. Project planning and execution
6. Testing implemented policies and procedures
7. Guidelines & Best Practices
8. Communication with Top management on business risks and threat scenarios
7. Guidelines & Best Practices
9. Advise on security Policy and SOPs
10. Regular review of security posture for any new systems or processes adoption
11. Implement and manage a cyber security program tailored to fit the organization’s business needs
12. Define and implement security and compliance governance.
13. Provide threat analysis and draft counterstrategy
14. Revise security policies and procedures
15. Manage Information security risks
16. Provide evaluation of threats and remediation
